In this guide, I will put together an example attack against one of metasploitable’s vulnerable Linux virtual machines. If you plan on replicating this, you must ensure you do not expose the metasploitable VM to the outside network otherwise anyone may attack your machine. On VMware there is a “Host-only” setting for your network adapter you want to apply. This will allow you to attack the metasploitable machine from your Kali VM without reaching the internet. Enjoy the following example:
1 – Host Identification – In this example we already know our host’s IP address to be 192.168.146.129 but if this was a company across the internet you may have found the IP with tools like Dig, Whois, or Ping. In this stage I will ping my target to ensure I have connectivity.

2 – Service Enumeration – To identify possible attack vectors I will use Sparta to conduct targeted Nmap scans which will enumerate open ports, what services are running, and the most likely operating system. Sparta will additionally begin to conduct follow-on enumeration against the available services by running tools like Nikto, Enum4Linux, and Nmap NSE scans. When sparta is done you have a user friendly graphical interface storing the outputs of these tools. In the example below, you can see the target is running dozens of services. Each of these services may have a misconfiguration or vulnerability which we can use to either further enumerate the box or gain remote code execution.

3 – Organize the Attack Surface – At this point, you should make a list of all potential attack surfaces and rank order them in likelihood of a vulnerability. Creating a rank structure may take some experience to do accurately but you will quickly learn basic services like SSH and RDP are far more likely to be secure than HTTP or SMB. In the example below, I used Kali’s default keepnote tool to keep track of the very large attack surface this target presents. Keepnote allows you to organize all your recon information for various targets, take screenshots, and add relevant files containing the scripts you have used so you can recreate any progress you have made.

4 – Analyze The Services – Now that we have our list, we should start exploring our most likely vector into the system. This can involve google, searchsploit, or enumeration tools built into Kali. First on our list is the Samba service. By right clicking on the service in sparta I can select Enum4Linux which will run several enumeration tools. Part of the output, listed below, displays that the specific server is Samba 3.0.20.

5 – Find Potential Exploits – Armed with this new information, turn to google to see if there is a public exploit available for this Samba version. The first google return is from rapid7.com which databases all the public metasploit modules available on kali. The next few returns are from exploit-db which contains over 35,000 public exploits. When conducting a penetration test or CTF you will find documented exploits for services and applications that haven’t been patched.

6 – Check Exploit Viability – Opening the rapid7 link below we see that this public module exploits a command execution vulnerability in the Samba version running on our target. It shows the module location at “exploit/multi/samba/usermap_script” in the msfconsole.

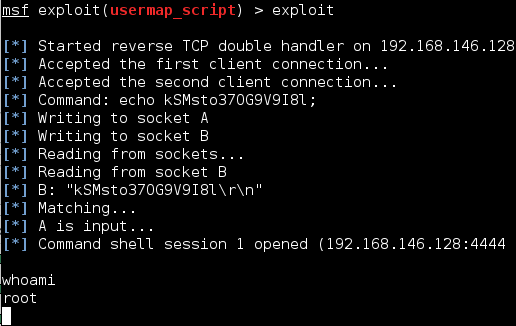
7 – Execute Exploit – Time to open our metasploit framework with msfconsole in the terminal. Once the framework opens, set the exploit module you want with the “use” command and the target with the “set RHOST” command. Demonstrated below, you can execute the module with the “exploit” command which will trigger the vulnerability and return you with a remote shell with root privileges. At this point you own the box and can begin any post exploit activities.

Conclusion
Using this methodology you can continue to probe through the different services for exploits or misconfigurations to see if you can manipulate them to get a shell. If this Samba service was current and had no exploit available you would move to the next service on your list. Exploits will not often be this straightforward and will require research into the vulnerability being attacked. You may need to set different options available on metasploits “show options” or “show advanced options” commands. The exploit may also be a standalone python script you need to modify or in C code which you will have to compile. Every exploit is a unique puzzle for you to figure out.