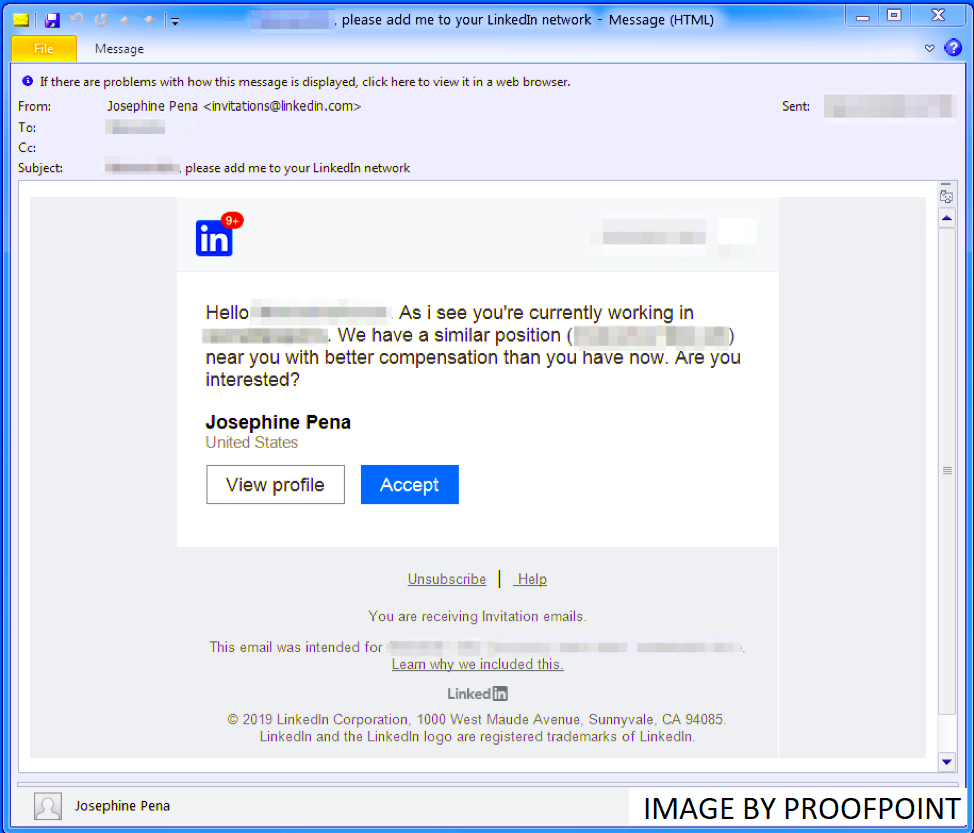
Researchers at the ProofPoint Threat Research Team recently released a report detailing the growing trend of hackers abusing LinkedIn to pose as legitimate recruiters interested in hiring them for their next position. The hackers reach out through LinkedIn’s direct messaging service, pretending to be a staffing company with an offer of employment for someone with the direct skills of the victim. For anyone who has a LinkedIn profile, this is a common occurrence which would not immediately set off any red flags.
To further legitimize the phishing attack, the malicious actor will build a fake website to impersonate the staffing company and direct the “applicant” to it for further information. When the interested victim browses to the website they will be served a malicious payload containing the More_eggs backdoor. The hackers would also try to follow up LinkedIn messages with emails to the victim containing malicious attachments that would infect the victim if they enabled macros.
When analyzing these fraudulent LinkedIn accounts, Dell SecureWorks shows the effort an Iranian Advanced Persistent Threat team went through to develop believable personas who would pass a cursory inspection by a suspecting victim. They break them into “Leader” personas and “Supporter” personas where “Profiles for Leader personas include full educational history, current and previous job descriptions, and, sometimes, vocational qualifications and LinkedIn group memberships. Of the eight Leader personas identified by CTU researchers, six have more than 500 connections.”
This new style of phishing attack shows the growing sophistication of threat actors as they transition away from shooting out mass emails and focus on targeted and believable attacks. By mimicking real scenarios where a stranger would reach out to you as a professional, your guard is down, and you are far more likely to download the attachments or browse to the malicious links.
These tailored phishing attacks have already been successful at gaining an initial foothold into companies. Redbanc, the company responsible for running all the ATMs in Chile, recently issued a public admission that they were breached via an employee responding to a developer role offered through LinkedIn. The attackers in this instance set up a follow-up Skype call for an interview and tricked the employee into downloading a malicious ApplicationPDF.exe file which infected the victim’s computer.
Now is a good time to inform your employees they may be the target of a phishing campaign through social media in addition to emails. It’s important to note that reputable companies will rarely require you to download documents directly from an email or a website and a quick google search will help ensure you end up at the right website. Due diligence is extra important when dealing with individuals you do not know directly, even if they are offering you a major raise and your dream job.