Before you can execute your first exploit you need to get set up with the right environment. For any beginners, Kali Linux is the best place to start. It is an open source Linux distribution that comes complete with the tools necessary to begin advanced penetration testing. To get running with your own Kali environment, […]
John the Ripper is one of the most common and powerful password crackers on the market. John has a Pro version which includes some extra useful features but most of the prime functionality a pentester needs can be found in its free version. John is able to take dozens of different password hashes, pilfered from […]
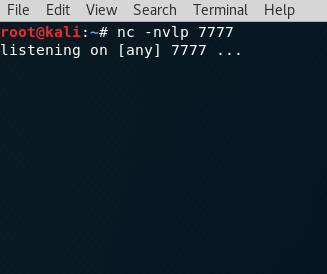
Netcat is a tool that can read and write TCP and UDP ports. This tool may not strike you as impressive but its simple and effective nature has made it so ubiquitous that it has been known as the Hacker’s Swiss Army Knife. It is regularly used to connect to a target service, port scan, […]
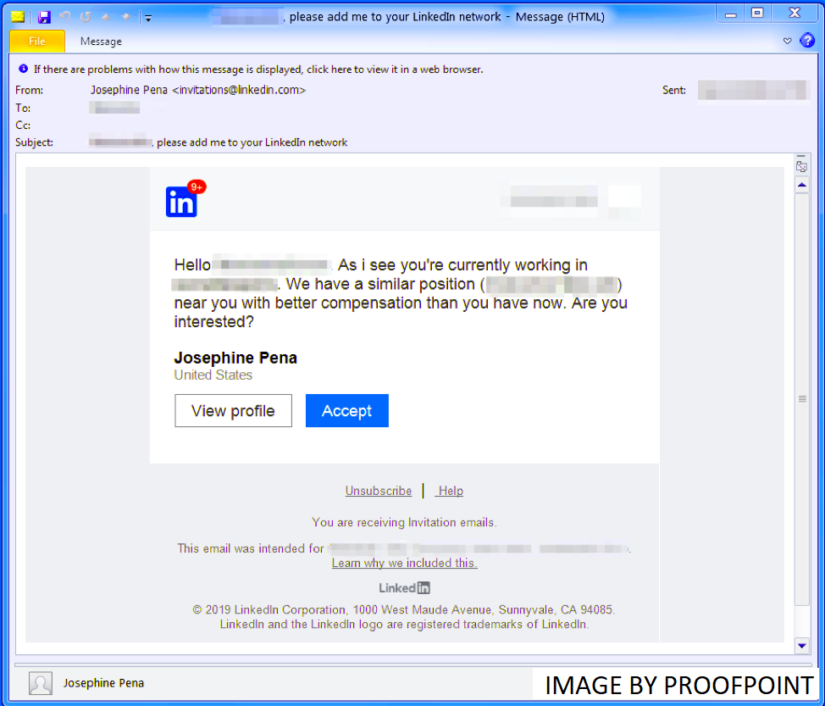
As the never-ending cat and mouse game advances in the world of cyber security we have seen a novel growth in the methodologies of malicious actors to avoid the ever-growing list of defensive products on the market. According to the annual 2019 IBM X-Force Threat Intelligence Index, cybercriminals have decreased their reliance on malware and […]