As the never-ending cat and mouse game advances in the world of cyber security we have seen a novel growth in the methodologies of malicious actors to avoid the ever-growing list of defensive products on the market. According to the annual 2019 IBM X-Force Threat Intelligence Index, cybercriminals have decreased their reliance on malware and instead have focused on using legitimate administrative tools like PowerShell and PsExec. While these techniques have been around for decades, they have grown to account for over 57 percent of cyberattacks in the past year and are something security teams need to start taking a closer look at.
This trend towards tools like PowerShell makes total sense and is something we can anticipate continuing. PowerShell is an extremely robust scripting language that has the ability to quickly and effectively accomplish nearly any task an administrator or hacker wants to accomplish. Due to this, IBM X-Force IRIS found complete malicious toolkits comprised entirely of PowerShell scripts. It also has two major benefits over traditional malware.
First, as an administrative tool, PowerShell is less likely to raise any flags as an indicator of compromise because it is something legitimate administrators would be using on a regular basis. Most Endpoint Detection and Response (EDR) solutions on the market are designed to look for anomalous activities on each system but a hacker who is living off the land with native tools can effectively blend into the environment and avoid detection.
Second, by leveraging scripts, a hacker can run entirely in memory without ever needing to place malware on the disk. According to the IBM report, this enables “malicious actors who use it to forego the file system and inject malicious code directly into memory, thus enhancing obfuscation, and often evading security controls designed to detect malware deployments.” This requires a new approach to security solutions entirely.
To protect against this growing threat, security architects can start implementing some quick and effective measures to minimize the effectiveness of the attack. Three of the top ways are:
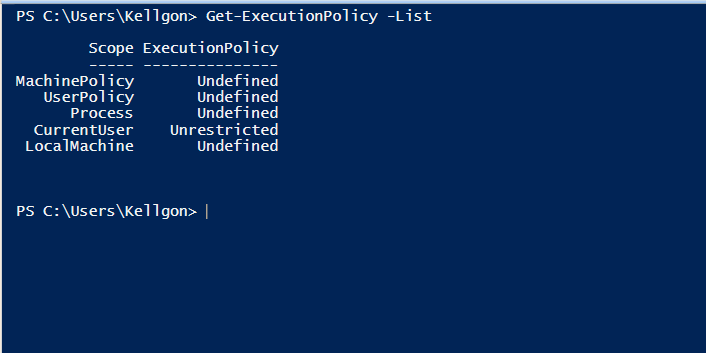
- Reduce the number of accounts who can use PowerShell to only those who need it with the Set-ExecutionPolicy cmdlet
- Treat PowerShell scripts like an executable that needs to be pre-signed
- Include PowerShell in your SIEM through continuous logging and monitoring
Whichever way an organization decides to treat this threat, this is a growing trend we will continue to see.